Widespread Exploitation of Oracle Vulnerability
CrowdStrike has identified an ongoing mass exploitation campaign leveraging a previously unknown zero-day vulnerability, now designated CVE-2025-61882, in Oracle EBS (E-Business Suite) applications. The campaign, active since at least August 9, 2025, is focused on unauthorized data exfiltration from compromised systems. Oracle publicly disclosed the vulnerability on October 4, 2025, confirming its capacity for unauthenticated remote code execution (RCE).
Threat Actor Attribution and Tactics
CrowdStrike Intelligence links the campaign with moderate confidence to the threat group GRACEFUL SPIDER, known for orchestrating mass exploitation attacks. On September 29, 2025, GRACEFUL SPIDER reportedly contacted multiple organizations, claiming to have accessed and extracted data from their Oracle EBS instances. The group used known email addresses and the “Clop” branding to bolster their claims, and is believed to have provided victims with evidence of data theft.
However, the involvement of other actors cannot be ruled out. A Telegram post on October 3, 2025, referenced collaboration among groups including SCATTERED SPIDER, SLIPPY SPIDER, and ShinyHunters, and included a purported Oracle EBS exploit. The post criticized GRACEFUL SPIDER’s methods, but the origins and usage of the exploit remain unclear.
Technical Details of the Attack Chain
Analysis of the attack sequence reveals a multi-stage exploit. The initial compromise begins with an HTTP POST request to /OA_HTML/SyncServlet, exploiting an authentication bypass—sometimes involving administrative accounts. Attackers then target Oracle’s XML Publisher Template Manager, sending GET and POST requests to /OA_HTML/RF.jsp and /OA_HTML/OA.jsp to upload and execute a malicious XSLT template. Execution of the template establishes outbound connections from the Java web server to attacker-controlled infrastructure, typically over port 443.
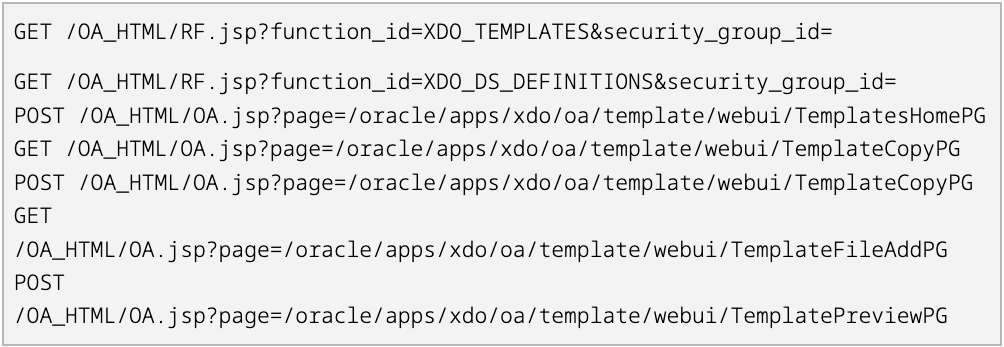
In most observed cases, these outbound connections are used to load web shells, granting the attackers persistent remote access. In one incident, a two-step process involving FileUtils.java and Log4jConfigQpgsubFilter.java was used to set up a backdoor, invoked via a public-facing endpoint. The full extent of these techniques is still under investigation.
Proof-of-Concept and Patch Release Escalate Risks
On October 3, 2025, a proof-of-concept (POC) exploit was publicly disclosed, coinciding with Oracle’s release of a patch for CVE-2025-61882. Oracle’s advisory, while not explicitly confirming exploitation in the wild, provided indicators of compromise (IOCs) such as IP addresses and malicious files, suggesting active abuse. CrowdStrike’s analysis indicates that the POC aligns with observed attack patterns, particularly those involving Java Servlets.
CrowdStrike assesses that the publication of the POC and the availability of a patch will “almost certainly encourage threat actors—particularly those familiar with Oracle EBS—to create weaponized POCs and attempt to leverage them against internet-exposed EBS applications.” Organizations are urged to apply the patch immediately and monitor for signs of compromise.
Ongoing Investigation and Outlook
CrowdStrike’s investigation into the root cause and scope of CVE-2025-61882 exploitation is ongoing. The company has high confidence that at least one threat actor is using this zero-day for widespread attacks, but the possibility of multiple actors exploiting different vectors remains. The uncertainty is compounded by the sharing of exploits in underground forums and the observed collaboration between various cybercriminal groups.
Given the critical nature of Oracle EBS in enterprise environments and the technical sophistication of the exploit chain, the campaign poses a significant risk to organizations with unpatched, internet-facing deployments.
