TL;DR
- CrowdStrike has enhanced its Falcon sensor for Linux to better detect sophisticated web shells.
- New features provide visibility into obfuscated and in-memory PHP web shells.
- The “On write script file visibility” feature has already led to hundreds of web shell detections.
- These improvements aim to prevent data exfiltration and lateral movement by attackers.
What’s New / Why It Matters
Web shells are a persistent threat, acting as powerful remote access tools for attackers targeting Linux servers and containers. They enable actions like process execution and data exfiltration, often remaining undetected for extended periods. CrowdStrike has introduced significant enhancements to its Falcon sensor on Linux platforms specifically designed to combat these advanced threats.
These updates focus on providing deeper visibility into PHP web shells, including those that use obfuscation techniques or operate in memory. This is crucial for organizations relying on Linux servers for business-critical web applications, as a successful web shell deployment can have devastating consequences, from data breaches to ransomware attacks.
Advanced Web Shell Detection on Linux
The core of CrowdStrike’s enhanced defense lies in two key features for the Falcon sensor on Linux: “On write script file visibility” and “Enhanced PHP visibility.” The “On write script file visibility” feature offers a proactive approach by monitoring script files as they are written to the file system. This method provides context and content awareness, surpassing traditional scanning techniques.
This feature has proven highly effective, with the CrowdStrike Falcon Adversary OverWatch team detecting 492 web shells in just three months. It allows security teams to identify malicious scripts, including previously unknown web shells, and gain a clearer understanding of an adversary’s actions during an incident. For instance, understanding the type of web shell used can reveal the extent of an attacker’s capabilities, such as gaining tunneling access without process execution.
Enhanced Visibility for PHP and Java Web Shells
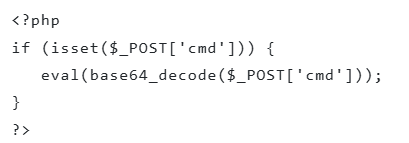
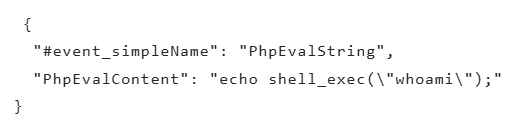
The “Enhanced PHP visibility” feature specifically targets the common use of the `eval()` function in PHP web shells, which dynamically executes code supplied by the attacker. This enhancement ensures that the use of `eval()`, along with variations like `assert()` and `create_function()`, generates a `PhpEvalString` event. This event includes the script content to be executed, offering security teams immediate insight into the web shell’s payload without requiring manual deobfuscation.
CrowdStrike also highlighted a sophisticated Java web shell observed targeting Zimbra mail servers. This attack involved writing a temporary malicious JSP file that used Java reflection to add a new filter. This filter could then execute malicious Java code from a staged JAR file, allowing the adversary to operate entirely in-memory and remove traces from the file system. This technique appears to be novel for Java-based web servers, mirroring similar advanced methods seen in .NET post-exploitation frameworks.
Investigating Web Shell Incidents with Falcon
When a web shell detection occurs within the Falcon console, analysts can leverage the “Investigate event” feature for deeper context. By filtering for specific event names like `NewScriptWritten`, `ScriptControlDetectInfo`, `PhpExecuteScript`, and `PhpEvalString`, security teams can reconstruct the adversary’s activity. This includes identifying the script’s file path, the process that wrote it, the full script content, and the evaluated content of obfuscated functions.
CrowdStrike provides example Advanced Event Search queries for their Next-Gen SIEM, enabling defenders to actively hunt for web shells using these new visibility features. These queries focus on commonly used functions associated with web shell process execution, empowering security teams to proactively search for threats.
How to Protect Yourself
- Ensure the CrowdStrike Falcon sensor is installed and updated on all Linux endpoints.
- Verify that the “On write script file visibility” prevention policy setting is enabled.
- Confirm that the “Enhanced PHP visibility” feature is activated within your Falcon policies.
- Regularly review security alerts and investigate web shell detections promptly using the Falcon console.
- Utilize the provided Advanced Event Search queries to proactively hunt for web shell activity.
- Stay informed about emerging web shell techniques and update security strategies accordingly.
Availability & Pricing
These enhancements are available now as part of the CrowdStrike Falcon sensor for Linux platforms. Specific pricing details are not announced but are typically part of CrowdStrike’s subscription-based security services.
Techswire’s Take
CrowdStrike’s latest advancements in its Falcon sensor for Linux underscore the escalating sophistication of web shell attacks. By providing granular visibility into obfuscated and in-memory threats, the company is equipping security teams with critical tools to detect and respond to these evasive threats more effectively.
The proactive “On write script file visibility” feature, coupled with detailed insights into PHP execution, represents a significant step forward in defending against persistent threats that often bypass traditional security measures.
