- Microsoft Entra Permissions Management (MEPM) will be retired on October 1, 2025.
- Enterprises relying on MEPM must seek alternatives for cross-cloud identity visibility.
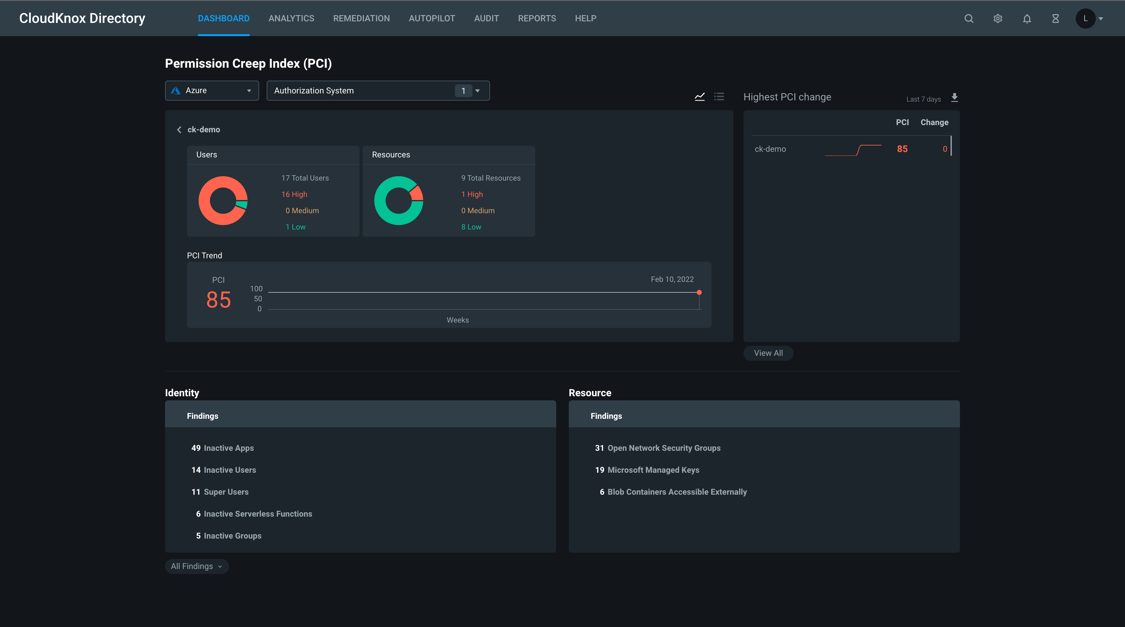
- Loss of MEPM raises risks of overprivileged accounts in multicloud environments.
- Vendor-neutral CIEM solutions are now essential for comprehensive permissions oversight.
End of Support for MEPM Poses New Security Challenges
Microsoft has announced it will retire Microsoft Entra Permissions Management (MEPM) effective October 1, 2025, a move that will impact organizations relying on Azure Entra ID for identity management across cloud platforms. MEPM has been widely adopted by Fortune 500 companies to identify excessive permissions, enforce least privilege, and secure both human and machine identities within their digital environments.
Currently, many enterprises use Entra ID as their primary identity provider, but their operations often span multiple clouds, including Azure, AWS, and Google Cloud Platform (GCP). MEPM has enabled these organizations to maintain a unified inventory of permissions, making it possible to detect and remediate overprivileged accounts and ensure compliance with security best practices.
Loss of Cross-Cloud Visibility
With the retirement of MEPM, organizations will lose the ability to view and manage permissions across different cloud providers from a single console. While Azure’s native identity and access management (IAM) features will remain, these are limited to the Azure environment and do not extend to other platforms.
For example, a global healthcare provider using MEPM to monitor effective permissions across Azure and enforce least privilege for both employees and automated services will now have to rely solely on Azure IAM. This change can create blind spots in environments where data lakes or applications are integrated with AWS or GCP, increasing the risk that overprivileged accounts go undetected and sensitive data is exposed.
Multicloud Risk Scenarios
The risk is particularly acute for enterprises with complex, multicloud architectures. A Fortune 500 retailer, for instance, may use Azure Entra ID for workforce identity while core supply chain applications run in AWS. Machine identities often bridge these environments, enabling automated processes and AI systems to interact across platforms. Without a cross-cloud CIEM tool, overprivileged AWS service accounts could be exploited, allowing attackers to move laterally from AWS into Azure—a technique seen in recent multicloud breaches.
Temporary permissions granted for development or migration projects can also persist long after their intended use, especially when machine identities are not tracked in a unified way. Without comprehensive visibility, organizations risk accumulating excessive privileges that could be leveraged in an attack.
Vendor-Neutral CIEM Now Essential
Industry experts stress that the end of MEPM makes vendor-neutral Cloud Infrastructure Entitlement Management (CIEM) solutions a necessity. These tools provide a continuous, accurate view of permissions and entitlements across all major cloud platforms, helping organizations enforce least privilege and reduce attack surfaces.
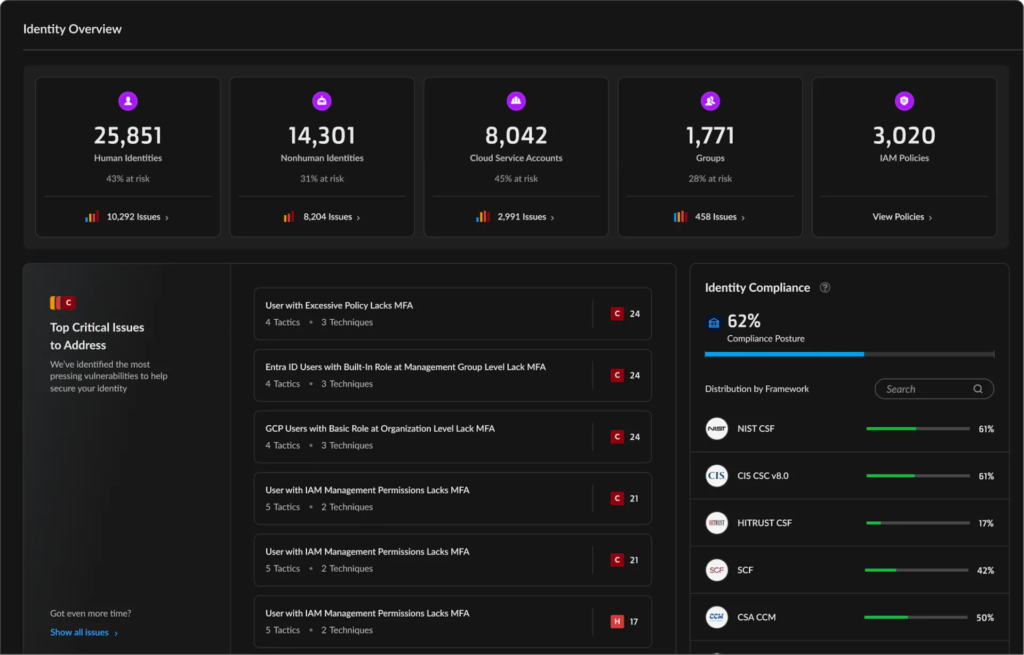
Products such as Cortex Cloud Identity Security offer full CIEM capabilities for Azure, AWS, and GCP, delivering a single source of truth for permissions across the entire cloud estate. This unified approach is critical for organizations seeking to maintain security and compliance in the absence of MEPM’s cross-cloud features.
Next Steps for Enterprises
With the October 2025 deadline approaching, organizations are advised to assess their current identity security posture and plan for the transition away from MEPM. This includes evaluating alternative CIEM solutions that can provide the necessary cross-cloud visibility and control.
Failure to adapt could leave cloud environments exposed to privilege escalation, lateral movement, and data breaches—risks that are only expected to grow as multicloud adoption increases.