Surge in Fraudulent Domain Registrations
As anticipation builds for the 2026 FIFA World Cup, cybercriminals are laying the groundwork for widespread scams. Since August 1, 2025, over 4,300 new domains referencing FIFA, the World Cup, or host cities have been registered. These domains, while seemingly innocuous in isolation, display patterns of mass, synchronized registration and share similar naming conventions and DNS infrastructure. This suggests a coordinated effort rather than random fan activity.
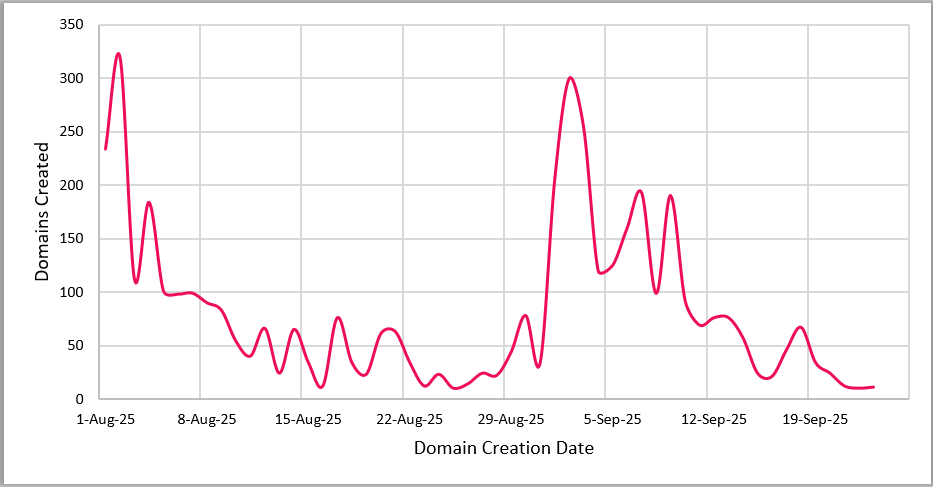
Nearly 1,500 domains were registered in just five days between August 8 and 12, 2025, with another spike in early September. Such concentrated activity points to automated, bulk domain procurement, a hallmark of organized cybercrime. The majority of these domains were registered through a small group of retail registrars, notably GoDaddy, Namecheap, Gname, Dynadot, and Porkbun. These registrars are favored for their scale, promotional pricing, and support for bulk automation.
Domain Tactics and Geographic Targeting
Attackers are not only targeting the upcoming 2026 event. Some domains reference future tournaments—2030 and 2034—employing a tactic known as domain aging. By registering domains years in advance and leaving them dormant, threat actors hope to build legitimacy before activating them for fraudulent campaigns.
The domain names reveal deliberate targeting of both global and local audiences. References to host nations—the United States, Mexico, and Canada—and host cities such as Dallas, Miami, Toronto, Vancouver, and Mexico City are common. These geographic cues are intended to boost search relevance and credibility, particularly for travelers seeking official information.
Linguistic segmentation is also evident. English dominates domains related to illicit streaming, aiming for global reach. Spanish and Portuguese are prevalent in ticket and merchandise scams targeting Latin American fans, while French domains appear in smaller clusters likely aimed at European supporters.
Types of Scams and Infrastructure
The fraudulent domains generally fall into three categories: counterfeit ticket sales, illicit streaming, and fake merchandise. Some sites focus on a single scam, such as selling non-existent tickets, while others combine multiple lures—offering both “streaming” and “tickets”—suggesting the use of template-driven generation kits for rapid deployment.
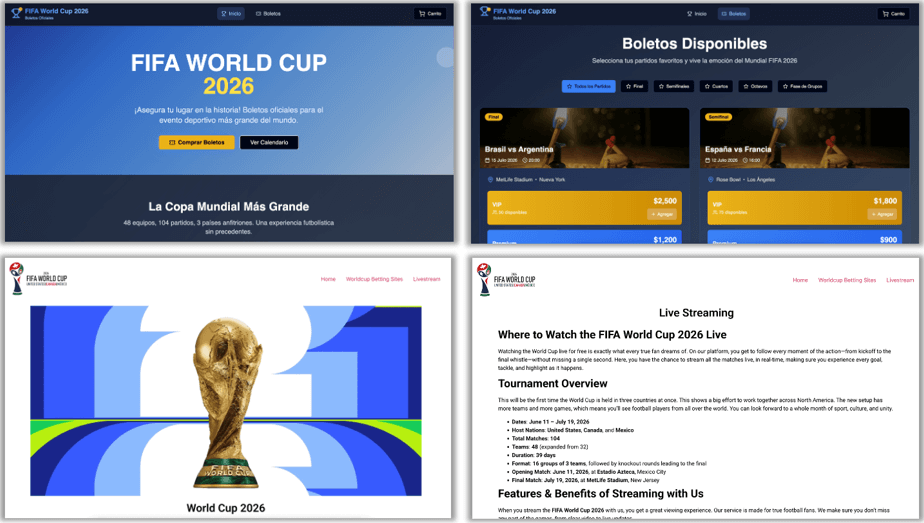
Streaming-related domains use keywords like “HD,” “watch live,” and “gratis” to attract viewers, while ticket scams, though less numerous, pose higher financial risks per victim. Merchandise scams, particularly those marketing jerseys and apparel in Spanish and Portuguese, are also widespread.
Analysis of DNS records reveals repeated use of identical nameservers across clusters of domains. This overlap, combined with synchronized registration patterns, indicates that a small number of semi-professional operators are managing large portfolios of fraudulent sites.
Beyond Domains: Ecosystem of Fraud
The threat extends beyond domain infrastructure. Telegram channels have already begun advertising “exclusive tickets” and counterfeit jerseys, while dark-web forums offer both fraudulent tickets and toolkits for conducting phishing or payment fraud under the FIFA brand. Social media platforms are expected to play a major role in driving traffic to these sites, with some pages posing as “official” outlets. Malicious ads in search results could even outrank legitimate FIFA websites, increasing the risk for unsuspecting fans.
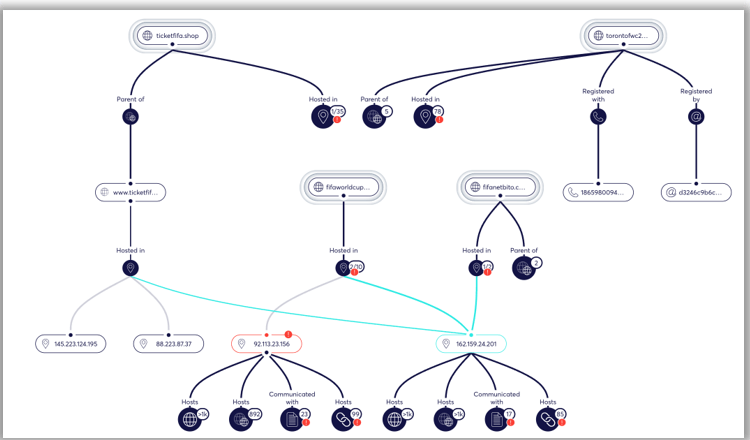
These activities form an interconnected ecosystem of fraud, stretching from domain registrations to underground marketplaces and mainstream social channels.
Systemic Threats to Ticketing Infrastructure
Perhaps most concerning are the systemic threats to FIFA’s own ticketing systems. Evidence suggests that botnets are being prepared to flood ticket queues, acquire inventory at scale, and resell tickets at inflated prices. These bot-driven surges also distort dynamic pricing algorithms, causing legitimate fans to face higher costs. In parallel, dark-web vendors are selling specialized bot kits, proxy farms, and account bypass guides tailored for FIFA’s infrastructure.
With the tournament still months away, the current activity represents the assembly of a sophisticated fraud infrastructure rather than the scams themselves. The scale and coordination observed underline the need for robust cybersecurity measures and heightened vigilance among fans and organizers alike.
