TL;DR
- A new threat group, Amaranth-Dragon, has been identified conducting cyber espionage in Southeast Asia.
- Campaigns targeted government and law enforcement agencies, often timed with local political events.
- The group shows strong similarities to APT-41, suggesting a potential affiliation.
- Amaranth-Dragon rapidly weaponized the WinRAR vulnerability CVE-2025-8088.
- Strict geographic targeting and sophisticated lures were employed.
What Happened
Check Point Research has uncovered a series of sophisticated cyber espionage campaigns that have been active throughout Southeast Asia since March 2025.
These operations, attributed to a newly identified threat group dubbed Amaranth-Dragon, specifically targeted government institutions and law enforcement agencies in countries including Cambodia, Thailand, Laos, Indonesia, Singapore, and the Philippines.
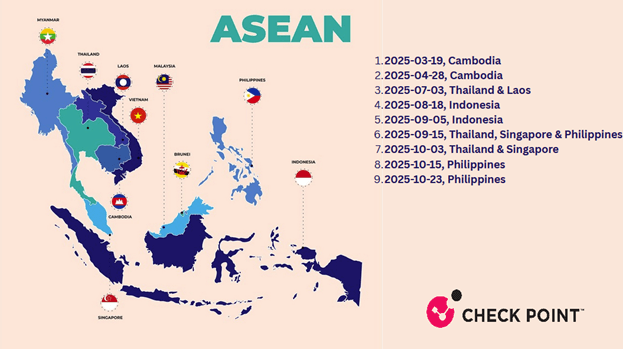
The campaigns were characterized by their precision, with attackers meticulously timing their activities to coincide with sensitive local political developments, official government decisions, or regional security events.
Impact
The primary impact of these campaigns is the potential for long-term geopolitical intelligence collection against targeted governments and law enforcement bodies. By leveraging highly tailored lures and exploiting vulnerabilities rapidly, Amaranth-Dragon aimed to gain persistent access to sensitive information.
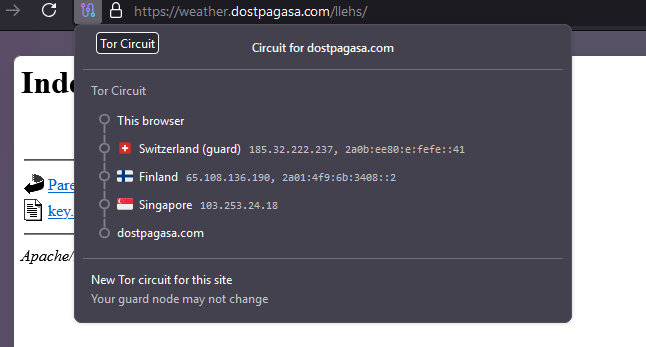
The group’s strict geographic enforcement, rejecting connections from outside intended target countries, suggests a focused and well-resourced operation designed to minimize detection and maximize intelligence yield.
Amaranth-Dragon’s Tactics and Sophistication
Amaranth-Dragon’s operational methods indicate a high degree of technical maturity and preparedness.
A notable example of their speed was the rapid incorporation of the CVE-2025-8088 vulnerability, affecting WinRAR, into live campaigns within days of its public disclosure and exploit code appearing online. This swift weaponization underscores the group’s agility in adapting to new security weaknesses.
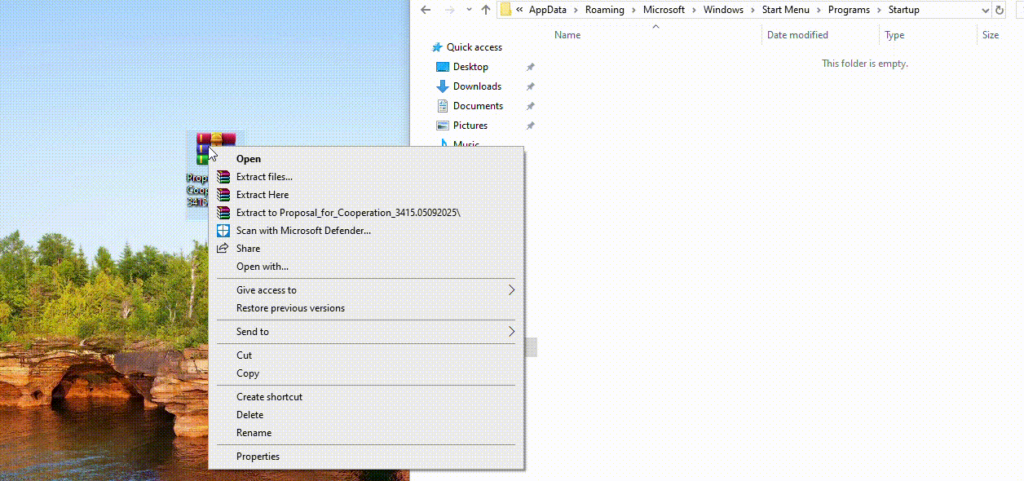
The campaigns employed sophisticated social engineering techniques, with malicious archive files often hosted on legitimate cloud platforms to appear more trustworthy.
The attackers also demonstrated a strong understanding of the geopolitical landscape, tailoring their lures to local events such as government salary announcements or joint regional exercises. This precision targeting, likely delivered via phishing emails, significantly increased the likelihood of victim engagement.
Links to APT-41
Technical and operational indicators strongly suggest a connection between Amaranth-Dragon and APT-41, a well-known Chinese-affiliated cyber espionage group. Both entities share a focus on Southeast Asian government and law enforcement targets, as well as similar methodologies in tool development and campaign execution.
Furthermore, patterns in infrastructure management, operational timing, and development practices point to a team operating within the UTC+8 time zone. These overlaps lead researchers to believe Amaranth-Dragon is either closely affiliated with or operating as a component of the broader APT-41 ecosystem, potentially extending espionage efforts under a new operational guise.
The findings highlight how modern cyber espionage merges speed, precision, and geopolitical objectives. Vulnerabilities are weaponized rapidly, and tailored phishing attacks can bypass traditional defenses. For government agencies and sensitive organizations, this underscores the critical need for rapid patching, robust visibility into file-based threats, and comprehensive layered security across endpoints and communication channels.
Check Point’s Harmony Endpoint and Harmony Email & Collaboration solutions are designed to assist organizations in mitigating exposure to such targeted attacks.
How to Protect Yourself
- Prioritize Patch Management: Implement a rigorous and rapid patching strategy for all software, especially widely used utilities like WinRAR, to address newly disclosed vulnerabilities promptly.
- Enhance Email Security: Deploy advanced email security solutions that can detect and block sophisticated phishing attempts, including those using malicious archives hosted on cloud platforms.
- Strengthen Endpoint Protection: Utilize advanced endpoint detection and response (EDR) solutions that provide deep visibility into file-based threats and can detect suspicious activity indicative of espionage tools.
- Implement Layered Security: Ensure security measures are in place across multiple layers of the network, including network perimeter, internal systems, and communication channels, to create a defense-in-depth strategy.
- Conduct Regular Security Awareness Training: Educate employees about the risks of phishing and social engineering, emphasizing the importance of scrutinizing suspicious emails and attachments, even if they appear to come from legitimate sources.
- Monitor for Suspicious Activity: Maintain continuous monitoring for unusual network traffic, unauthorized access attempts, and the presence of unknown or suspicious files on systems.
Techswire’s Take
The emergence of Amaranth-Dragon and its apparent ties to APT-41 signal a continued evolution in state-sponsored cyber espionage. The group’s ability to rapidly weaponize vulnerabilities and conduct highly targeted, geographically restricted campaigns underscores the increasing sophistication and geopolitical motivations behind these operations. Organizations in vulnerable sectors, particularly in Southeast Asia, must remain vigilant and adapt their security postures to counter these persistent and adaptive threats.
For full technical details, campaign timelines, and indicators of compromise, readers are encouraged to consult the complete Check Point Research report.
